The 128th Installment
Problems with My House Key
by Hiroshi Koyama,
Professor
Have you ever been locked out of your home because you forgot your house key? This has happened to me many times. Calling the management company or staying somewhere overnight is troublesome, and more importantly, it is depressing to think about later. I have kept a spare key in my bags for a long time, and while locking myself out has become less frequent lately, it sadly happens once every few years. Recently, I added a smart lock after seeing an article on a graduate's Facebook page. The newest ones can even be used with the auto-locking doors of apartment buildings, and you do not even need to operate your smartphone if you place an NFC tag. It is a true modern convenience. However, this just means that my lifeline is now my smartphone, and it is all over if my Wi-Fi goes down. There are stories of people returning to cash after an earthquake shuts down the electricity and destroys electronic money. Smart locks are great, but assuming the worst, they add to the confusion. It is going from high tech to low tech, but I wonder if I should put up a box with a lock that unlocks using three to four dials and stores my key. You know, the little one where the keys are often kept when going to look for a new apartment.
◎ Brute Force Attacks
Since there are 1,000 possible three-digit key combinations, a patient and deliberate brute force attack could disarm it in a maximum of 1,000 seconds (16 minutes and 40 seconds) if it took one second per process. That explains why there are so many stolen bicycles. The personal identification numbers (PINs) for banks and credit cards have traditionally been four digits since I was born [1]. With 10,000 four-digit number combinations, it takes up to 10,000 seconds (2 hours, 46 minutes, and 40 seconds), which seems slightly stronger, but if a brute force attack is carried out using digital technology instead of physically turning the dials, the system could be unlocked in less than 100 seconds (or 0.01 seconds per process). This is weak. Banks often tell you to avoid four-digit pin numbers that can be easily guess such as birthdays. One’s own birthday would be obvious, but the number of possible four-digit number combinations drop to 366 if a date is used. Even if patterns where the month and day are reversed are included, the number of combinations is 588, which is less than the strength of three-digit keys. This is too weak.
Four-digit PIN estimation is discussed in [1]. This article looks at about 1800,000 four-digit PINs for accounts leaked from a website in 2009. The most frequently used PIN at 3.7% was 1234, while 8439 was the least common at 0.0006%. Fig. 1 shows the two digits before and after the four-digit PIN being displayed in XY coordinates.
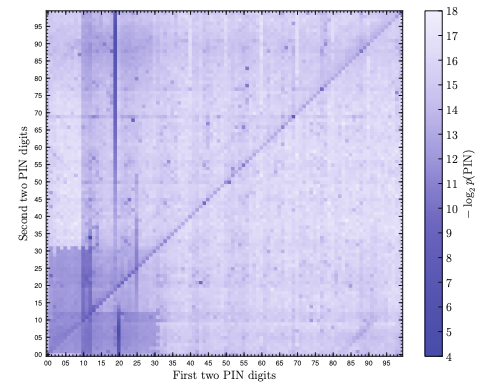
Fig.1: Four-digit PIN distribution map leaked from RockYou
The four digits with higher frequencies of occurrence are darker, and the following can easily be predicted.
· The date ranges in a MMDD format from 0101 to 1231 and reverse DDMM format in the lower left corner are darker. Consequently, the numbers for the 31st of months and the end of February are lighter.
· ABAB formats such as from 0000 and 0101 to 9898 and 9999 are clearly shown as a straight line from the bottom left to the top right, and AAAA formats such as 7777 and 8888 are particularly dark.
· The vertical line on the left is birth years 1930 to 2010.
· In addition to 1234, which is the most frequent, 2345, 3456, 4567, 5678, 2468, and 4321 are also darker.
Interesting speculations were made on Twitter, such as that the 5150 near the center was attributed to Van Halen’s album [2]. If you are interested, you may want to check the darkness of the four-digit pin you are using.
◎ Architectural Control
How can the strength of pin numbers be increased? The following systems are commonly used as architectural control.
1.For authentication that is too weak today, such as four-digit PINs, there is a set maximum number of errors to prevent brute force attacks. It seems that if you incorrectly enter the password to unlock the screen on iOS 6 times, you have to wait for one minute, then five minutes, 15 minutes, and 60 minutes. Then, if you get it wrong 10 times, you are instructed to connect the iPhone to iTunes, and all of the data could be deleted at worst (I do not have the strength to try this today.). There is a slight drawback in setting a maximum number of errors: even third-party operations can lock accounts after incorrectly entering PINs a few times. Actually, someone locked one of my accounts last year this way (I do not know if it was malicious or not, but it is annoying, so please stop playing pranks.).
2.On iOS, the default number of digits for the pin was changed from four to six (1,000,000 possible six-digit combinations). Recently, PINs are often limited to a string of at least 8 numbers and lower and upper case letters (about 2 x 1014 combinations). If it is allowed, setting as long a PIN as can be remembered would be best. PINs with only 15 numbers are stronger than 8-digit PINs with numbers and upper and lower case letters.
Which is the right choice for an architectural decision? And what other mechanisms would be practical? There needs to be a balance between strength and usability with implementation constraints when determining the architecture.
◎ Reverse Brute Force Attacks
When building information systems for financial institutions, standards set by The Center for Financial Industry Information Systems (FISC) stipulate limits on the number of times a PIN can be entered incorrectly, and account are locked to defend against malicious attacks. However, around last summer, it was pointed out that there may have been a reverse brute force attack in which there was a target PIN of 1234 or another number, and accounts were tested continuously by brute force. In this attack, each account is attacked only a few times, so it is difficult to defend against by setting a maximum limit. Because high-frequency PINs are known to some extent, it is relatively likely that this will succeed. However, I hear that recent account management is monitoring behavior with AI and the like.
◎ Fundamentals of Discrete Mathematics
Counts of how many combinations there are, which have appeared several times in this article, are the basis of discrete mathematics and are required for the Code Crack Problem, Traveling Salesman Problem, n Queens Problem, and other problems which are all typical examples of information science, and are also important in the recently popular AI domain. Although the fundamentals of counting, as the law of sums and products, substitution, permutations, and the like, are a part of junior high school mathematics, a quick review of the changes in the high school mathematics curriculum shows that content related to counting was removed from the mandatory curriculum in the 1998-1999 and 1977-1978 revisions. In terms of age, these generations of students are around 30 years old (born between April 1987 and March 1996) and 50 years old (born between April 1966 and March 1978, which includes me). In addition, even if it is mandatory, there is a risk that students may have forgotten mathematics and other subjects from junior high school. It would probably be a good idea to review some high school math again. In the first semester, “Information Architecture Theory 1” will cover a review of the basics of discrete mathematics, so feel free to join.
[1] Joseph Bonneau, et al., A Birthday Present Every Eleven Wallets? The Security of Customer-Chosen Banking (2012). https://link.springer.com/chapter/10.1007/978-3-642-32946-3_3
